Let’s have
some fun
Secure doesn't have to be boring. The COLDCARD Mk4 comes in a variety of colors to match your style.
Shop Colors

128x64 pixel OLED screen

Entering pin is easy & quick

Protects screen and prevents
hardware implants

Tap to transmit all data types

Real crypto security chips

Secure doesn't have to be boring. The COLDCARD Mk4 comes in a variety of colors to match your style.

The industry-standard for transmitting both data and power over a single cable.

Maximum security when transferring data between devices.

Secure & very short-range wireless transmission that sends data to your phone easily
COLDCARD can emulate a USB disk drive, so sending PSBT files can be a drag-n-drop.

PushTx allows single-tap broadcast of freshly-signed transactions from COLDCARD to a phone.

Like the classic calculators from our childhoods: slide the protective cover down, reverse, and slide back onto the rear. Saves your screen from damage!





 Q
Q
 Mk4
Mk4
We find it quite scary that some hardware wallets trust the main microprocessor with their most valuable secrets. Instead, COLDCARD uses two Secure Elements, from different vendors, to protect your Bitcoin.
Specifically, the COLDCARD uses Microchip's ATECC608 and Maxim's DS28C36B, to store the critical master secret: the 24-word seed phrase for your BIP39 wallet.
For your funds to be compromised, a backdoor would need to exist for 3 different chips: both the Secure Elements, and the main microprocessor.
 Q
Q
 Mk4
Mk4
To resist Evil Maids, and other sneaky people with physical access to your COLDCARD, we sign our firmware with a factory key. During boot-up, the firmware's signature, and nearly every byte of flash memory, will be verified and the appropriate Green/Red light set.
Changing that light's status is actually controlled by dedicated circuitry connected directly to a Secure Element, so a rogue bit of software cannot override it. The circuit for the lights is exposed on the top surface of the product, so any physical tampering by those maids will be visible as well.
 Q
Q
 Mk4
Mk4
The PIN code on COLDCARD is divided into two parts, such as 1234-5678. You first enter 1234 and then you will be shown two words on-screen. Those words are unique for all PIN prefixes, and for each COLDCARD ever made. (The secrets used to enforce that come from inside the secure element, and are unknown to the rest of the world.)
Your job is to memorize those two words, keep them secret, and every time you use the COLDCARD, check them before entering the final 5678 part of your PIN. This protects you against a trojan-horse COLDCARD that might look like yours but it cannot know those two words.
 Q
Q
 Mk4
Mk4
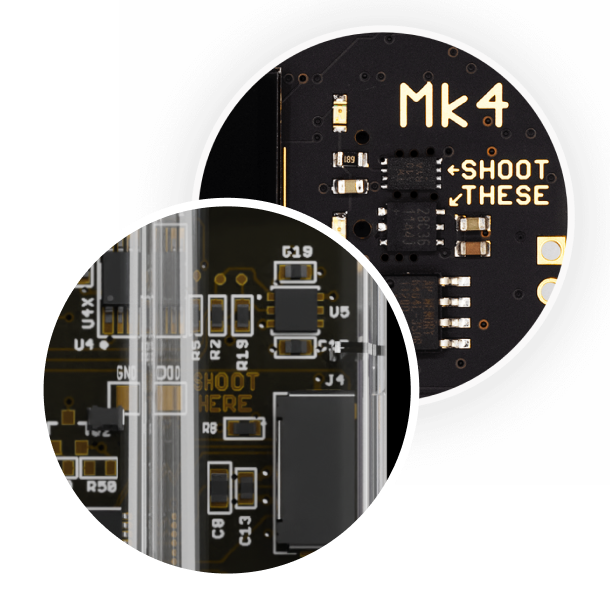
The carefully designed PCB increases the SE probing difficulty. Our clear case is part of our security model too, so you can look and see if a "hardware implant" has been inserted inside your device.
Because of the in-depth use of the secure elements, there is no "factory reset" for the COLDCARD. If you forget your COLDCARD PIN, there is nothing we can do except remind you to recycle your e-waste responsibly!
We've even put a label, "SHOOT THESE", for more effective device destruction... When the time comes.
 Q
Q
 Mk4
Mk4
COLDCARD never needs to touch a computer. It can work entirely from a USB power pack or AC power adapter. This includes everything you need to do in the whole life of the product:
• Initial PIN choosing and setup.
• Pick your 24-seed words using our TRNG, import existing secrets, or use your dice rolls.
 Q
Q
 Mk4
Mk4
If you don't trust our random number generator, you can generate the BIP39 seed phrase using dice rolls. We help with this process: you just have to press 1–6 for each roll (99 rolls recommended). At the end of that process, you'll have a properly-encoded seed phrase based solely on the dice rolls. Learn how to verify COLDCARD's dice-rolls math here.
COLDCARD has even more tricks up its sleeve!
You may define an optional "duress PIN code". If anyone enters that PIN code, instead of the "real" PIN code, nothing special is shown on the screen and everything operates as normal... However, the bitcoin key generated is not the main key. It is effectively a completely separate wallet!
To take best advantage of this feature, you should put some Bitcoin into the duress wallet. How much you are willing to lose or what you need to make it plausible, we don't know.
The "duress" wallet will still be derived from the original BIP39 words, so you don't need to back it up separately, but there will be no way to get from that wallet back to the original wallet with the real funds in it.
This is a covert variation of the BRICK ME PIN mode. It forces a time delay (of minutes/hours/days) when logging into the Coldcard.
But once set, unlike the normal countdown, this special mode covertly bricks the Coldcard (or, optionally merely wipes the seed). Again, this may form some part of your game-theory for duress situations, but is completely optional.
The goal of this mode is to provide plausible deniability of a required time delay (similar to Bank's safes), while denying the attacker a functional device in case they take it away.
We support BIP39 passphrases so you can also create an unlimited supply of distraction wallets. This feature is also useful for your own organization of funds or accounts. Unlike the single duress PIN, an unlimited number of related wallets can be created using BIP39.
Another PIN can also be defined, which we call the “Brick Me” PIN. Using that PIN code at any PIN prompt, will destroy the dual secure element and render your Coldcard worthless. Again, this may form some part of your game-theory for duress situations, but is completely optional.
Force a time delay when logging into the Coldcard. Once enabled, you must enter the PIN correctly, and then wait out a forced delay (of minutes/hours/days) while a countdown is shown on-screen. Then enter your PIN correctly, a second time, to get in.

We use a unique tamper-evident plastic bag to package your new COLDCARD. Each bag is unique and coded with a serial number. That "bag number" is written into the COLDCARD's as it's put into its bag. That value cannot be changed, and we ask your to verify the bag number when you power-up the COLDCARD for the first time.

The clear plastic case on COLDCARD is an important feature as well. There have been demonstrations of inserting custom hardware inside a competitor's hardware wallet to capture key-presses.
Temporary seed is a temporary secret completely separate from the master seed, typically held in RAM and not persisted between reboots in the Secure Element.
Seed Vault adds the ability to store multiple temporary secrets in encrypted settings for simple recall and later use. Stored secrets are AES-256-CTR encrypted with your master seed's key.
COLDCARD Co-Signing (CCC) is a powerful feature that lets you create automated multisig wallets, protected by user-defined spending policies for enhanced security and control.
When enabled, CCC adds a second seed (the Spending Policy Key) to your COLDCARD, which works with your main seed and additional backup keys to create 2-of-N multisig wallets.
The spending policy acts like a hardware security module (HSM), enforcing rules such as transaction limits, spending frequency, whitelisted addresses, and optional 2FA authentication—giving you flexibility while protecting your funds.